- What is Port Scanning and Why Is It Important for Security
- How Administrators Use Scanning to Find Open and Vulnerable Ports
- How Masscan and Nmap Help in Security Auditing
- How Closed or Misconfigured Ports Can Lead to Data Leaks
- Best Scanning Practices for Protecting a Corporate Network
- Conclusions
- Comparative Table
What Is Port Scanning and Why Is It Important for Security
Hello, buddy! Today I want to share some important insights about port scanning – one of the key tools for ensuring the security of servers and networks. You may have already heard that checking open ports helps identify potential vulnerabilities, but let’s dive into why it is so crucial. Port scanning is the process of determining which ports on a server or network are open, what services are running behind them, and how well they are protected against unauthorized access. In today’s world, where cyberattacks are becoming increasingly sophisticated, regular port monitoring is an essential measure to protect corporate infrastructure and personal data.
When we talk about scanning, we mean not only looking for open entry points but also assessing how the services are configured, what vulnerabilities might be exploited by attackers, and what measures should be taken to mitigate risks. This process helps administrators identify unnecessary or misconfigured services that could become gateways for attacks. That is why regular port auditing becomes a fundamental part of any organization’s security strategy.
For a visual representation, I recommend taking a look at this diagram that demonstrates the process of port scanning and network monitoring:
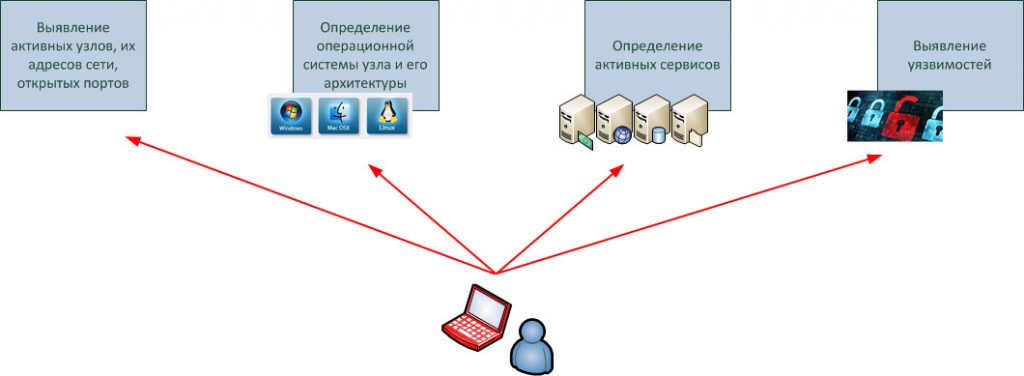
How Administrators Use Scanning to Find Open and Vulnerable Ports
Network and server administrators have long understood that before an attacker finds a way into the system, it is essential to check for vulnerabilities themselves. Port scanning allows them to quickly determine which services are accessible from the outside, as well as to identify unnecessary open ports that could become “holes” in security. Using specialized utilities, professionals not only detect the presence of open ports but also analyze how well network filters and firewalls are configured.
For example, many IT specialists regularly conduct checks using tools like Nmap or Masscan. They run automated tasks that help detect unplanned changes in network configuration. This approach enables them to react quickly to emerging threats and promptly close vulnerabilities. Additionally, port scanning helps optimize server performance by identifying unnecessary open ports, thus reducing load and improving overall network efficiency.
To perform a basic scan with Nmap, you can use the following command:
nmap -sV -p 1-65535 192.168.1.0/24This command scans all ports in the specified range, determines the versions of the services, and allows you to quickly assess the network’s security status.
How Masscan and Nmap Help in Security Auditing
If you’re interested in security, you have probably already come across tools like Masscan and Nmap. Both are indispensable assistants in conducting security audits, yet each has its own unique features. Masscan is renowned for its speed – it is capable of scanning huge IP ranges in just seconds, which is especially useful when checking large networks. In contrast, Nmap provides much more detailed information about discovered services, their versions, and potential vulnerabilities.
Using these tools together allows you to obtain the most complete picture of network security. For example, you can first run Masscan for quick detection of open ports and then use Nmap for an in-depth analysis of the detected services. This combined approach not only helps quickly identify threats but also enables you to take specific steps to mitigate them.
To install Masscan on Linux, simply execute the following commands:
sudo apt-get update
sudo apt-get install git gcc make
git clone https://github.com/robertdavidgraham/masscan.git
cd masscan
makeAnd to install Nmap, you can use the official website: Download Nmap. If you are on Windows, download the precompiled version from their website and follow the installation instructions.
As Bruce Schneier once said:
“Security is not a product, but a process.” — Bruce Schneier
This wise quote reminds us that effective network protection requires constant monitoring and timely action.
How Closed or Misconfigured Ports Can Lead to Data Leaks
Often, it is the unnoticed, misconfigured, or outdated services that become an entry point for attackers. Even if a port is closed, errors in configuration or improper application of filters may allow cybercriminals to access confidential information. A simple example is when an outdated web server with known vulnerabilities is running on a server – an attacker can use an open port to infiltrate the system even if the overall security policy is correctly configured.
In such cases, regular port scanning plays a decisive role. Timely detection of these “holes” allows administrators to promptly close them, update the software, and adjust firewall settings. It is important not only to identify vulnerable ports but also to analyze the configuration of the services running on them. Often, even a small configuration error can lead to serious consequences, such as data leaks or complete system compromise.
To check for vulnerabilities, you can use Nmap with additional scripts, for example:
nmap --script vuln -p 1-65535 192.168.1.0/24This command allows you to identify potentially dangerous services and vulnerabilities in their configuration, which is an important step in preventing attacks.
Best Scanning Practices for Protecting a Corporate Network
When it comes to network security, it is important not only to perform one-off checks but also to implement regular monitoring that will help promptly detect and mitigate threats. Here are a few recommendations to help you organize effective port scanning in a corporate environment:
- Regular Scheduled Scanning: Set up automated tasks for periodic port checks. This will allow you to detect changes in network configuration and unnoticed vulnerabilities.
- Use a Combined Approach: Employ quick scanning with Masscan for initial detection of open ports, then conduct a detailed audit using Nmap.
- Analyze the Collected Data: Implement a system for logging and analyzing scan results so you can react quickly to emerging threats.
- Keep Tools and Software Updated: Stay informed about updates for Masscan, Nmap, and other utilities to use the most current versions with patched vulnerabilities.
- Train Employees: Regularly conduct training sessions for IT specialists so they know how to correctly interpret scan results and take appropriate measures.
Additionally, do not forget the importance of properly configuring firewalls and intrusion detection/prevention systems (IDS/IPS). These measures will help reduce the risk of exploiting vulnerabilities and provide an extra layer of protection for the entire network.
For example, to set up regular scanning, you can use cron jobs in Linux. Here’s an example of a task that will run Nmap every night:
0 2 * * * /usr/bin/nmap --script vuln -oN /var/log/nmap_scan_$(date +\%F).txt 192.168.1.0/24This command is set to perform a scan at 2 AM, saving the results in a log file with the date indicated, which is convenient for later analysis.
Conclusions
In this article, we have thoroughly discussed how port scanning helps protect servers and networks from attacks. We learned that:
- Port scanning is an effective method for detecting open and vulnerable entry points into a system, allowing for timely identification of threats.
- Administrators use this method for regular security audits, which helps prevent unauthorized access and data leaks.
- Tools such as Masscan and Nmap provide powerful functionality for fast and detailed network analysis, combining speed and accuracy.
- Misconfigured or outdated services can become a gateway for attackers, so regular scanning and updating of configurations are crucial.
- Implementing best scanning practices, including automation, log analysis, and staff training, contributes to a higher level of protection for corporate networks.
I hope that after reading this article, you have gained valuable insights into how port scanning can serve as a reliable tool in the fight against cyberattacks. Remember: security is an ongoing process that requires constant attention and improvement. Apply the knowledge you’ve gained and share it with your colleagues to ensure your network remains secure!
Comparative Table
| Tool/Approach | Pros | Cons | Links/Additional Content |
|---|---|---|---|
| Nmap |
|
|
Download Nmap |
| Masscan |
|
|
Masscan on GitHub |
| Scanning Automation (cron, scripts) |
|
|
Linux Cron Guide |
Попробуйте ScaniteX бесплатно!
Автоматизированная платформа для сканирования открытых портов и обнаружения активных сервисов в режиме онлайн.
Начните 24ч пробный период (промокод FREE10), чтобы протестировать все функции сканирования для безопасности вашего бизнеса.
Получить бесплатный триал



Комментарии