Introduction
Port scanning is one of the key methods for analyzing network security that allows you to determine open ports on a specific IP address. It is an essential tool for system administrators, cybersecurity specialists, and even curious users who want to understand how their network works. In this article, we will provide a detailed explanation of how to perform IP port scanning using popular tools such as Nmap. You will receive a step-by-step guide that will help even beginners understand this process.
The goal of this article is not only to explain how to perform the scan, but also to teach you how to interpret the results so that you can use them to improve your network security. If you are ready to dive into the world of network analysis, let’s get started!
What Is Port Scanning and Why Is It Used?
Port scanning is the process of checking the status of ports on a specific IP address or device on a network. Each port is associated with a specific service or application, and its state (open, closed, or filtered) can reveal a lot about the device’s security.
The main objectives of port scanning are:
- Security assessment: Identifying vulnerabilities in the network infrastructure.
- Network diagnostics: Detecting connectivity issues or service unavailability.
- Vulnerability detection: Discovering open ports that could be exploited by attackers.
Port scanning is a powerful tool, but its use must be ethical and legal. Remember that scanning networks without permission may result in legal consequences.
“Security is a process, not a product.” — Bruce Schneier, cybersecurity expert.
Preparing for Port Scanning
Before starting port scanning, you need to be prepared. You will need:
- Scanning tools: Nmap, Angry IP Scanner, Advanced Port Scanner, and others.
- Basic networking knowledge: Understanding of IP addresses, ports, and protocols.
- Legal permission: Ensure that you have the right to scan the chosen IP address.
Scanning other networks without permission is against the law and can lead to serious consequences. Always adhere to ethical standards and use your skills responsibly.
Step-by-Step Guide to Port Scanning
Now that you are ready, let’s move on to the practical part. We will cover the process of port scanning using Nmap — one of the most popular tools for this task.
Step 1: Choose a Scanning Tool
Nmap is a powerful and versatile tool that supports many port scanning features. You can download it from the official website.
Step 2: Installation and Configuration
After downloading Nmap, install it on your computer. The installation process is simple and intuitive. For Windows, an installer file is available, and for Linux and macOS, you can use package managers.
# Installation of Nmap on Ubuntu
sudo apt-get update
sudo apt-get install nmap
Step 3: Enter the IP Address for Scanning
After installation, open a terminal or command prompt and enter the command to scan the ports. For example:
nmap 192.168.1.1
Here, 192.168.1.1 is the IP address you want to scan.
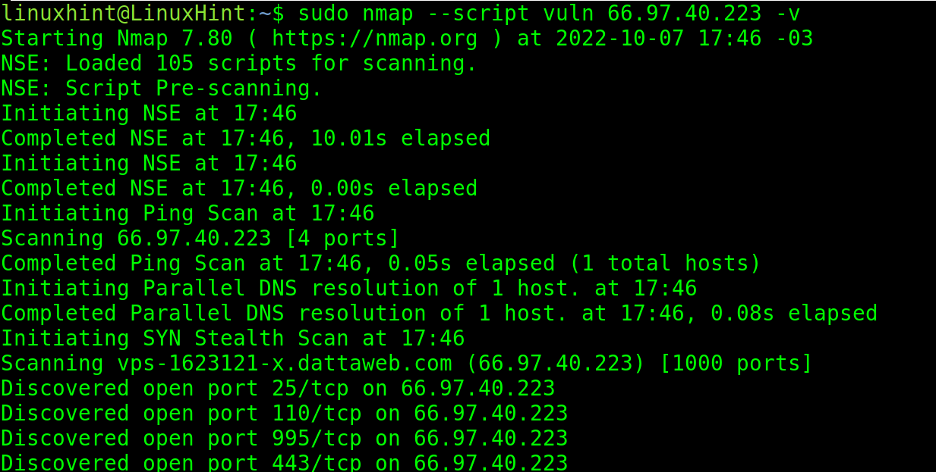
Step 4: Run the Scan and Interpret the Results
After running the command, Nmap will begin scanning and output the results. Example output:
Starting Nmap 7.92 ( https://nmap.org ) at 2024-09-01 12:00 UTC
Nmap scan report for 192.168.1.1
Host is up (0.002s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
This output shows which ports are open and which services are running on them.
Step 5: Analyze the Open Ports
Open ports may indicate potential vulnerabilities. For example, if port 22 (SSH) is open, ensure that a strong password and two-factor authentication are in use.
Nmap Usage Example for Port Scanning
Let’s consider a more complex example using Nmap. Suppose you want to scan all ports on an IP address and get detailed information about the services:
nmap -p 1-65535 -sV 192.168.1.1
This command scans all 65,535 ports and detects the versions of the services running on them.
Safety and Ethics
Port scanning is a powerful tool, but its use must be responsible. Here are a few tips:
- Always obtain permission before scanning someone else’s network.
- Use the scan results to improve security, not for malicious purposes.
- Regularly update your tools to use the latest features and fixes.
Conclusions
In this article, we discussed how to perform an IP port scan using Nmap. You learned how to choose a tool, install it, run a scan, and interpret the results. Now you can use this knowledge to analyze your network and improve its security.
Remember, port scanning is not just a technical process, but also a responsibility. Use your skills wisely and always adhere to ethical standards.
Frequently Asked Questions (FAQ)
Which ports are most commonly scanned?
Ports associated with popular services such as HTTP (80), HTTPS (443), SSH (22), and FTP (21) are most frequently scanned.
How can I protect my IP from scanning?
Use firewalls, close unnecessary ports, and regularly update your software.
What alternative tools exist for port scanning?
In addition to Nmap, you can use Angry IP Scanner, Advanced Port Scanner, and Masscan.
Additional Resources
- Official Nmap Documentation.
- The book “Nmap Network Scanning” by Fyodor.
Попробуйте ScaniteX бесплатно!
Автоматизированная платформа для сканирования открытых портов и обнаружения активных сервисов в режиме онлайн.
Начните 24ч пробный период (промокод FREE10), чтобы протестировать все функции сканирования для безопасности вашего бизнеса.
Получить бесплатный триал




Комментарии